As businesses continue to prioritize data protection and privacy in 2025, achieving SOC 2 certification has become a key goal for many organizations, particularly those in industries like tech, finance, and healthcare. However, achieving SOC 2 compliance is not as simple as filling out a few forms or checking boxes—one of the most essential components of the certification process is the cybersecurity audit.
A cybersecurity audit is an in-depth evaluation of your company’s information systems, policies, and procedures to ensure they align with the required SOC 2 Trust Services Criteria. In this blog, we’ll discuss the role of cybersecurity audits in SOC 2 certification, why they are crucial in 2025, and how your business can prepare for and benefit from these audits.
At Decrypt CPA, we specialize in guiding businesses through the SOC 2 certification process, ensuring you meet all necessary cybersecurity and compliance requirements. Let’s dive in and explore what you need to know.
What is a Cybersecurity Audit?
A cybersecurity audit is a comprehensive review of your organization’s security policies, infrastructure, and processes. The goal is to identify vulnerabilities and assess the effectiveness of your cybersecurity measures in protecting data, preventing breaches, and ensuring privacy.
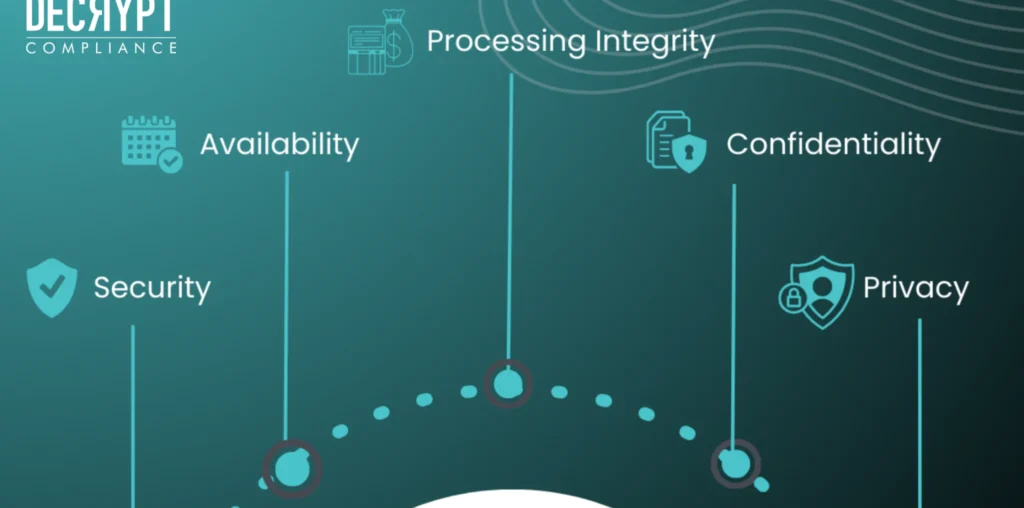
For SOC 2 certification, a cybersecurity audit specifically focuses on the Trust Services Criteria (TSC) that are relevant to information security, including security, availability, processing integrity, confidentiality, and privacy. These audits are typically conducted by third-party auditors who evaluate your organization’s systems and practices to ensure they meet SOC 2 requirements.
If you’re looking for expert assistance with cybersecurity audits in the context of SOC 2 certification, Decrypt CPA offers specialized services to ensure your organization is fully prepared for the audit.
The Role of Cybersecurity Audits in SOC 2 Certification
SOC 2 certification is based on the premise that an organization follows stringent security practices in managing sensitive client data. A cybersecurity audit plays a central role in assessing whether your organization is meeting these standards. Let’s take a closer look at the specific role a cybersecurity audit plays in the SOC 2 process:
1. Evaluating Security Controls
A major component of the SOC 2 audit involves assessing whether your business has the appropriate security controls in place to protect sensitive data from unauthorized access, breaches, or alterations. A cybersecurity audit will review the effectiveness of these controls, which may include:
- Firewalls and intrusion detection systems
- Encryption for data in transit and at rest
- Access controls for restricting unauthorized access
- Authentication processes, such as multi-factor authentication (MFA)
By evaluating your security controls, the audit ensures that your systems are secure and capable of preventing security threats.
At Decrypt CPA, we offer guidance on implementing strong cybersecurity measures to meet SOC 2 security standards.
2. Identifying Vulnerabilities and Gaps
A cybersecurity audit helps to identify vulnerabilities in your organization’s systems, policies, and procedures. This includes assessing the effectiveness of your data protection strategies and identifying any potential risks. For example, your audit may uncover gaps in:
- Employee training on security best practices
- Outdated software that could be exploited by attackers
- Weak access control policies that could allow unauthorized personnel to access sensitive data
Once vulnerabilities are identified, you can address them before undergoing the official SOC 2 audit. By fixing these gaps, you can significantly reduce your risk of a failed audit.
Action Tip: Regularly conduct cybersecurity audits to stay proactive about addressing vulnerabilities and strengthening your overall security posture.
3. Ensuring Compliance with SOC 2 Criteria
The SOC 2 Trust Services Criteria (TSC) focus on five key areas—security, availability, processing integrity, confidentiality, and privacy—which are all critical to achieving certification. A cybersecurity audit will specifically evaluate how well your business meets each of these criteria.
- Security: Are your systems protected against unauthorized access and cyber threats?
- Availability: Is your system available for use as committed or agreed upon with clients?
- Processing Integrity: Does your system operate with accuracy, completeness, and timeliness?
- Confidentiality: Are you safeguarding sensitive client data from unauthorized access?
- Privacy: Are you ensuring that personal information is handled according to privacy laws and regulations?
A cybersecurity audit will help identify any deficiencies in meeting these criteria and give you time to implement the necessary changes before your formal SOC 2 audit.
Decrypt CPA provides expert assistance in ensuring that your organization meets these critical SOC 2 requirements, helping you achieve certification without the stress.
4. Documenting Evidence for the SOC 2 Audit
During the cybersecurity audit, your organization will be required to provide detailed documentation and evidence of your security measures, policies, and procedures. This documentation is essential for the formal SOC 2 audit and will be used to demonstrate your company’s commitment to maintaining secure systems.
The cybersecurity audit will ensure that your documentation is comprehensive and up-to-date, covering areas such as:
- Security policies and procedures
- Incident response plans
- Data protection strategies
- Access control lists
Having solid documentation in place not only helps ensure a smooth audit process but also shows that your organization takes security seriously.
Action Tip: Keep your cybersecurity documentation updated and organized to ensure your SOC 2 audit process goes as smoothly as possible.
5. Mitigating Risk and Enhancing Business Reputation
One of the primary reasons for conducting a cybersecurity audit is to mitigate risk. By identifying and addressing potential vulnerabilities, you can prevent data breaches and security incidents that could damage your reputation, cost you customers, or result in regulatory penalties.
Successfully passing a SOC 2 audit can greatly enhance your reputation in the marketplace. Clients and partners are increasingly prioritizing security when choosing business partners, and having SOC 2 certification demonstrates that you’ve implemented industry-standard controls to protect data.
How to Prepare for a Cybersecurity Audit
Now that you understand the role of cybersecurity audits in SOC 2 certification, it’s time to focus on how to prepare for one. Here are key steps to ensure your business is ready for the cybersecurity audit and the eventual SOC 2 audit:
1. Conduct an Internal Review
Start by reviewing your internal systems and practices to identify any areas that may not meet SOC 2 requirements. This includes assessing your cybersecurity controls, policies, and procedures. A self-assessment will help you address potential issues before the audit.
At Decrypt CPA, we provide SOC 2 readiness assessments to help businesses evaluate their current security practices and ensure they are in line with SOC 2 requirements.
2. Work with Experts
Given the complexity of cybersecurity audits and SOC 2 compliance, it’s highly beneficial to work with experts who understand the intricacies of the certification process. Decrypt CPA can guide you through every step of the cybersecurity audit and SOC 2 certification process.
3. Document Everything
Ensure that your organization has thorough documentation of all security measures and protocols. This includes policies, incident response plans, access controls, and any other measures that demonstrate your commitment to cybersecurity.
4. Engage in Regular Security Reviews
Even after your audit, it’s important to engage in regular reviews and updates to your security practices. Cyber threats are constantly evolving, so it’s crucial to stay proactive in identifying new risks and improving your defenses.
Conclusion
Cybersecurity audits play a critical role in the SOC 2 certification process by ensuring that your organization meets the Trust Services Criteria and is effectively protecting sensitive data. By conducting thorough cybersecurity audits and addressing any gaps, you can improve your chances of successfully achieving SOC 2 certification and strengthening your business’s security posture in 2025.
If you’re ready to start your journey toward SOC 2 certification or need assistance with preparing for your cybersecurity audit, Decrypt CPA is here to help. Contact us today for expert guidance on achieving SOC 2 compliance and ensuring your organization is fully secure.